A lot of people spend the modern workday with headphones on or earbuds in, listening to music as they work or communicating through a headset. That makes it inevitable that these devices will get dirty. Let’s go over how these devices can be safely cleaned to get rid of the grime that nobody wants to be wearing on their head.
Argentum IT LLC Blog
Workplace burnout is a serious issue that can have far-reaching impacts in your business. Therefore, it is critical that you can identify when one of your team members is starting to feel it, and know what you can do to help reduce it. Let’s go over what can lead to burnout, as well as a few ways to remediate it.
Let me ask you something: how many people do you fundamentally trust? Well, in a zero trust network, that number is reduced to zero. The idea of such a network is that everyone, whether they’re operating inside of the network or out, needs to be verified… and as you might imagine, it has proven effective in preventing data breaches.
Most modern businesses rely on wireless internet connectivity in their day-to-day processes. Of course, this means that their potential productivity is tied to the quality of their internet and its capability to serve the entire workforce. As a business grows it becomes more important that its Wi-Fi setup can support it. Let’s go over the process of properly scaling your network to your needs.
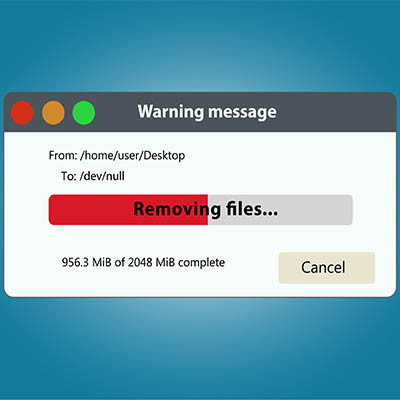
We’ve all been in a place where the storage on our computer fills up a little too quickly for our liking. While you could delete or store unused files in the cloud, there is another method that you can use to quickly free up a little extra space that you might not have realized is there. If you can delete temporary files, you might find that you suddenly have a lot more storage space to play around with on your computer.
Google Chrome is a very popular browser nowadays. In June of this year, for example, about 65 percent of the overall browser market share was attributed to Chrome. Seeing as so many people utilize Chrome, we thought it would be helpful to share a few tips that can help make Chrome even more productive for the user.
“Hackers are a serious threat to modern businesses” isn’t exactly a novel statement, is it? However, if a hacker was to be lurking on your network, would you know the signs to help you catch them? Just in case, we wanted to share a few strategies that can help highlight these warnings so you can more effectively catch any threats present on your network—particularly when your workforce is accessing it remotely.
While it isn’t officially a business solution, per se, the collaboration platform known as Discord has seen some popularity as a means of facilitating a business’ internal communications. Let’s go over some handy tips to improve your use of the platform, in case you are part of an organization that does so. Who knows… this might inspire you to give it a chance for yourself.
While spam filtering can be great for your business’ own defenses, the spam filtering that your contacts have in place could very well keep your messages from reaching them. This simply will not do. Let’s go over a few ways that you can help prevent your emails from being caught up in these filters before your contacts or prospects can read them.
While it really would be a nice thing to have, there is no magic bullet for your business’ cybersecurity—no single tool that allows you to avoid any and all issues. However, there is one way to help make most threats far less likely to be successful: building up your company’s internal security awareness amongst your employees and team members. Let’s go over eleven ways that you can help ensure your company is properly protected, simply by encouraging your employees to take a more active role in guarding it.
Most accounts these days require a password of some sort, and as such, the average user has countless of these codes that need to be kept both secure and top-of-mind. Some web browsers have built-in password management tools to help make them more user-friendly, but with so much convenience involved, one has to ask whether or not these built-in management tools are as secure as they should be.
Because of the protection it can offer your organization, data backup is a necessary tool for you to have—that is, provided it has the requisite security and reliability you’ll need should you ever have to lean on it. Let’s go over a few guidelines to help you be sure that your backup is trustworthy enough to stake your business’ future on.
With many—if not most—computers and especially laptops featuring integrated webcams at this point, it isn’t hard to imagine how disastrous it would be to be spied on through it. Let’s take a few moments and go over a few ways to be sure that your webcam isn’t being used without your consent by someone else.
If you are like many other people, your desktop computer just sits there, day after day, allowing you to run your business. Unfortunately, like any other machine, it will fail. One way to prolong the lifespan of your computer is to keep it clean. Today, we thought we’d give you some pointers on how to do so.
Every day, it seems like there’s a new threat to be concerned about. Obviously, there’s the big one that the whole world’s been dealing with, but there’s also the smaller things that we’re supposed to be worried about… like “blue light”, for example. What is that, and what can it really do?
As it turns out, blue light is more than just a marketing gimmick, and can potentially impact your health. Let’s go over a few tips to help you filter it out, and why you may want to do so.